Secure your digital services
The threat of cyber attacks has increased dramatically in recent years as more services go online. Software today must address identity and authentication, access control (authorization), confidentiality, and integrity at every level to minimize the risk and damage that could be caused by a security breach. It’s imperative that you secure your digital services.
We can help you to develop your digital services using these cornerstones:
Identity and access control
The identity is one of the core elements in a secure solution, maybe even the most critical component. If you do not know who is requesting your data, it is impossible to apply access control.
We can help you setup identity and authorization for your needs.

- Authenticators
An authenticator is the means used to confirm a user’s identity, that is, to perform digital authentication. Social media, BankId, and fingerprints are common ways to authenticate, but new techniques emerge that the solution need to adhere to.
- Authorization service
The authorization service produces a token that contains the user’s identity and information needed to perform access control (authorization). Think of the token as a ticket that gives you access to API:s, data, and services, the ticket controller validates the information on the ticket (authorization) before you are allowed to pass.
- User management
The authentication server needs to verify and access data related to the authenticated identity. Today’s online services are often complex combinations of several underlying systems, many times silos. The user management can be seen as a kind of user broker (SCIM) to sync users across these silo systems.
If you require any further information, feel free to contact us
API management & integration
The API:s are the digital interfaces of your business, both internally and externally. The API Manager becomes the central point that provides the API:s with documentation, measurements, and a defence line.
We can help you design API:s and setup API Manager to authenticate and authorize users and be the first line of defence of your services.
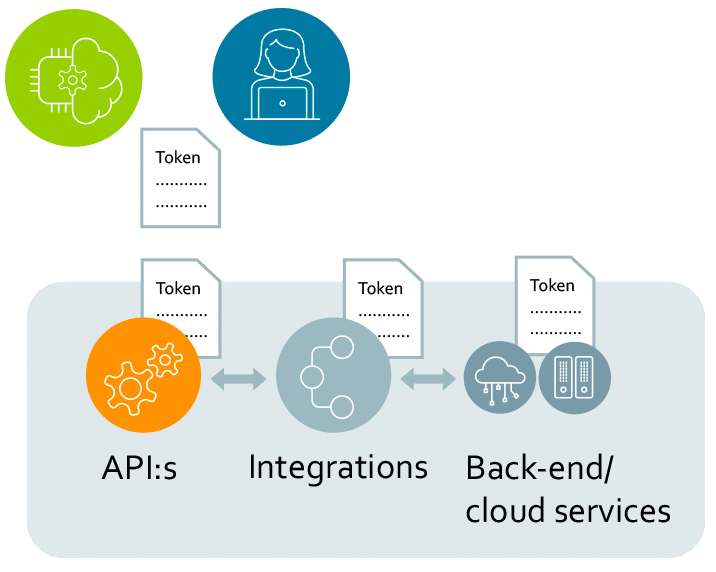
- API Manager
API management is the process of creating and publishing API:s, controlling access, collecting and analysing usage statistics, and reporting on performance.
- Tokens
API Manager trust and evaluates tokens issued by your token server to decide if the call should be let through or not.
- Developer portal
Collaboration platform for developers to access and test your API:s and provides the API documentation.
- Integration
We can all agree on that customer facing “public” API:s have to be secure but let’s not forget about the “internal” integration endpoints that may be publicly available and potential data leaks. The integration layer can also be used to secure data from legacy systems if they do not support modern authorization technologies.
If you require any further information, feel free to contact us
Secure Software development
Agile software development and DevOps are widely adopted methodologies to develop software; optimized for focus on functionality and short time to market. Unfortunately, security has not been a core concern of these methodologies. This has led to that developers have little or no guidance on how to develop secure software and that security is left to the very end of the project when time and cost constraints are at their maximum and short-cuts in the security implementation is far to common.
We can provide developers with a reliable security architecture consisting of best-practices and reusable well-designed software security components that will allow the team to keep focusing on customer value and time to market while still delivering secure software.
- Think security in all phases
Security should be thought of from beginning to end, through design, implementation and operations.
- Understand your service
It’s not until you understand your service end to end that you will have enough information to set the correct level of security. Who is the audience? How sensitive is the data? What level of access control do we need?
- Use standards, guidelines and proven technology
Build your service using best practice and rely on proven technology, incorrect implementation and use of open source components may itself become a security threat. Provide implementation guidelines and strategies for how the choose third party components and technologies.
- DevSecOps
DevSecOps routines with configuration management will secure the life cycle management of the software and surrounding environments.
If you require any further information, feel free to contact us
Regulations
It’s important to identify any regulations such as GDPR, PSD2, that could affect the service as early as possible. If there are any regulations to comply with, it’s important to enforce rules in the right place at the right time. That will minimize the risk of data leakage and that it is not possible to bypass it.
We can help you to analyze and classify data to take appropriate actions to comply with regulations. We can also help you to implement the controls according to best-practices and prepare the service for future changes.
Read our insight on PSD2.
Customer use cases

Banking
We have helped several banks to secure their APIs to comply with Payment Service Directive (PSD2) regulations. Banks are under constant pressure to comply with new regulations, especially in the EU. With the Revised Directive on Payment Services (PSD2) banks APIs will be open to third-party actors to build new applications around the financial institution. These API:s must use Strong Customer Authentication to comply with the PSD2 directive from the European Payments Council.
Read our insight on PSD2.

Public sector
We have helped multiple public sector customers to implement zero trust by introducing IdP/IAM-solutions established with a best of breed-approach. This has included establishing secure API-management and streamlining authentication procedures for applications and webservices. Other services have included providing efficient procedures for how attributes from business systems can be used in authorisation decisions support the management of complex distributed user catalogues.

Telemarketing
We helped a client to repackage existing services for reuse in online services. They had to secure and harden internal services to make them publicly available for self-service portals, enabling the customer to give end-users access to data and APIs. We provided insights and knowledge on how to organize the Identity and Access Management team (IAM) and which tools to use to provide fine-grained security.

Power and Utility
We built a layer of identity and access control in a customer-facing digital service to provide smooth login while protecting user data. The service made previously unavailable data available via an API Manager to support new customer-centric services including real-time energy consumption and power outage information.

Anders Essner
Phone: +46 (70) 513 56 19
anders.essner(at)ductus.se
