
INSIGHT
One Secure Organization – Centralized IAM as the Foundation for Physical and Digital Security
For many organizations, the realms of physical and virtual IT security are merging as companies look to digitalize more processes and create one secure organization. How, then, do you ensure the same protocols and high levels of security are applied to onsite visits, for instance, as to servers and virtual networks?
Common and complex problem
Whether it’s a mega factory, construction site, mine, or research laboratory, diverse external visitors come to sites regularly. Goods are delivered, printers, servers, and specialist equipment are serviced, drains are unblocked, consultants are on assignments, and client meetings take place. Large organizations can have hundreds of external people onsite at any given time.
We see this regularly and have developed a modern approach to identity and access management (IAM) to help solve the problem. It’s based on our experiences from supporting mining companies, banks and developing IAM software for use at test tracks for prototype vehicle testing.
Agile way of working
As all organizations are different, with very diverse ecosystems, policies, and regulatory frameworks, there isn’t a one-fits-all solution. Therefore, we apply a proven, stepwise approach to any deployment. By starting with a pilot project, we can implement and test a solution and apply lessons learned from the deployment as we move forward with onboarding applications and new use cases to the new secure architecture. This agile way of working is far more effective than spending many months developing a company-wide solution that may need considerable adjustments following deployment.
Three-tiered approach to IAM
But what is it? To best serve organizations with complex security requirements, a three-tiered approach is required. A technical platform, where the mechanics of the solution are managed; a framework, which governs how the system works and is managed; and DevOps, which ensures smooth and continuous operations and updates.
IAM Platform
- Identity Provisioning
- Identity to Account Linking
- Access Token Provisioning
- Policy Based Access Control
IAM Framework
- Governance
- Reference Architecture
- Taxonomy
- Guiding Principles
IAM DevOps
- Team
- Processes
- Tooling
Zero Trust identity management
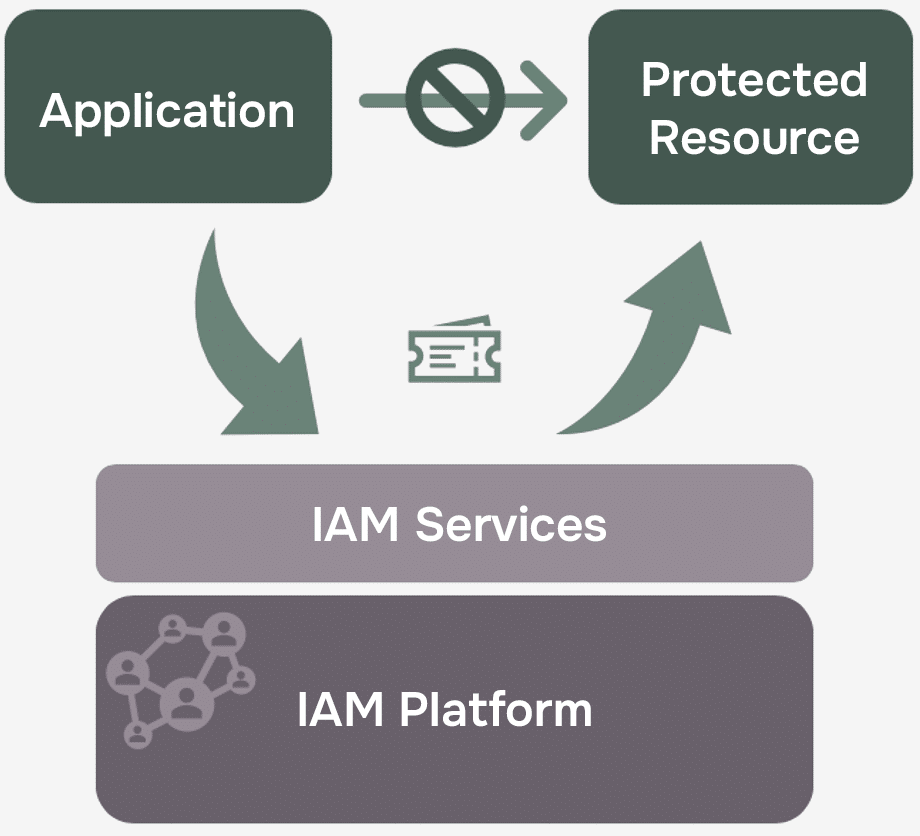
Based on a zero-trust philosophy, the IAM solution uses a token-based system to securely handle authentication and policy-based access control to manage authorization effectively. This ensures, for instance, that an application cannot directly access a protected resource on a user’s behalf. Instead, a central identity provider issues secure tokens to access resources when an application needs to identify a user.
Policy Based Access Control (also known as Attribute Based) is highly suitable for combining physical and virtual security as it offers fine-grained authorization that isn’t available in a role-based solution. This enables access to resources or property to be governed by location, time, date, assignment, company, nationality, and much more, in alignment with an organization’s policies.
Read part 2 in this series: One Secure Organization – Policy-Based Access Control (PBAC) for Enhanced Security.
Get started
If you recognize these issues or want to develop a single security solution for physical and digital security but don’t know where to start, our consultants can support you. We recommend you start with a particular pain point. Our team will define an IAM framework, with a reference architecture and guiding principles, and then we can begin to resolve the issues in a pilot project.
Don’t wait until it’s too late. Get in touch and let’s get started.

Anders Essner
Phone: +46 (70) 513 56 19
anders.essner(at)ductus.se
