
INSIGHT
A Blueprint for Network Automation: Designing Scalable, Secure, and Maintainable Architectures
Network automation isn’t just about speed — it’s about strategy. For large enterprises and service providers, scaling operations without escalating complexity is a constant challenge. Tools alone won’t solve this. Without a robust architecture, every layer of automation risks becoming another silo.
At Ductus, we’ve spent more than 15 years helping customers across industries design and deliver automation solutions that not only work — they scale. As a trusted partner, we guide organizations through transformation projects that bring agility, interoperability, and long-term value.
This insight outlines the foundational architecture we’ve developed and refined through years of real-world deployments. It is designed to help decision-makers and technical leaders understand the key layers, principles, and enablers of a scalable, secure, and maintainable automation approach—supporting both near-term agility and long-term transformation.
Why Architecture Matters More Than Tools
Most automation journeys begin with scripting — quick wins driven by skilled engineers. But scripting alone doesn’t scale. Maintenance becomes brittle, updates introduce risk, and the system grows harder to understand.
To avoid these pitfalls, organizations need a composable, vendor-agnostic, and API-first automation stack that enables:
- Cross-domain orchestration
- Reduced technical debt and faster rollout cycles
- Consistent operations across multi-vendor environments
A solid architecture allows you to evolve your tooling without re-engineering your entire automation strategy.
This need for flexibility is backed by industry research. An EMA report (Network Management Megatrends 2020) found that organizations most successful with automation often credited a multivendor approach—integrating best-in-class tools rather than relying on a single vendor.
This highlights the importance of designing a modular, interoperable architecture that can evolve with technology and business demands.
Key Building Blocks of a Modern Automation Stack
The following core architectural layers form the backbone of a scalable network automation strategy. Together, they enable a seamless flow from accurate data modeling to orchestrated change execution.
Each layer contributes to a tightly integrated, end-to-end automation lifecycle.
Network Source of Truth (NSoT)
The foundation of a reliable automation system is a single source of truth that coth the physical and logical aspects of your network. The NSoT should:
- Accurately model physical (PNI) and logical (LNI) infrastructure
- Be extensible to support custom attributes and service relationships
- Offer robust APIs for real-time data access and updates
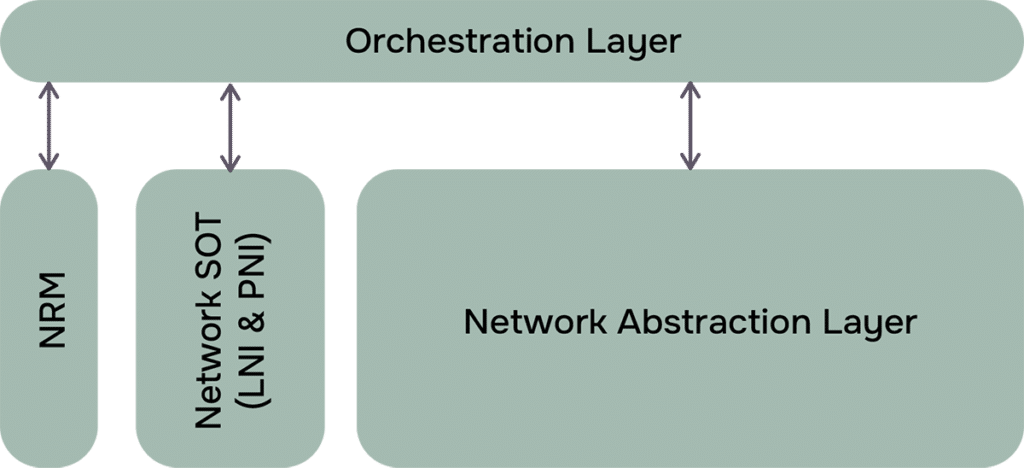
A strong NSoT improves data consistency, drives collaboration across teams, and enables scalable automation. This consideration is especially important at the strategic level, where aligning automation with long-term business goals is key.
Examples:
- NetBox for streamlined physical modeling
- Nautobot for advanced plugins and extensibility
Network Resource Management (NRM)
NRM expands beyond IP address management to cover all dynamically allocated network resources like VLANs and identifiers.
- Should integrate seamlessly with your NSoT
- Enables pre-validation of resource availability
- Supports allocation, reclamation, and lifecycle tracking
A modern NRM strategy ensures resource efficiency, reduces manual errors, and supports automated provisioning. This is especially critical for leaders aiming to ensure automation delivers measurable operational impact.
Examples:
- phpIPAM for lightweight IP space tracking
- NetBox/Nautobot for full-stack inventory and resource control
Orchestration Layer
Orchestration provides the engine that executes workflows across your infrastructure. It handles:
- Task coordination and dependency management
- Error handling and rollback
- Human-in-the-loop interactions (approvals, escalations)
Orchestration impacts time-to-market. A well-designed layer allows operations teams to deliver services faster, with fewer errors. This is particularly relevant when aligning automation capabilities with leadership goals and investment planning.
Tools we’ve implemented include:
- Itential IAP for telco-grade orchestration
- Camunda for general-purpose process workflows
- Cisco Workflow Manager for vendor-aligned service automation
Network Abstraction Layer (NAL)
A vendor-neutral abstraction layer simplifies complexity by exposing only the required capabilities of each device or domain.
- Bridges configuration differences across vendors
- Provides a clean interface to the orchestration layer
- Supports model-driven and intent-based automation
A well-implemented NAL reduces lock-in and increases the reusability of automation logic. This aligns directly with strategic efforts to build automation that is scalable, flexible, and aligned with long-term operational goals.
Examples:
- Cisco NSO for high-scale, multi-vendor abstraction
- Inmanta for declarative service orchestration
- Ansible for smaller-scale or simpler environments
- Clixon Controller for model-driven programmability in multivendor Linux-based environments, with an open-source foundation
Strategic Enablers for Long-Term Success
API-First Approach
At the heart of any future-proof automation strategy lies an API-first mindset. This principle ensures that all components — from orchestration to inventory systems — are designed for composability and integration from day one.
Automation thrives on integration. API-first components enable composability:
- Seamless integration with service portals, CI/CD, OSS/BSS systems
- More testable, scalable, and secure automation
- Clear interface contracts for teams
API-first is not just a preference — it’s a foundational design principle that ensures every layer of the automation stack can expose and consume APIs consistently. This principle is what makes it possible to later introduce an API layer on top of the stack: a strategic interface that exposes automation workflows for self-service, integrates securely with external systems, and enables central governance through API gateways or service meshes.
By combining API-first design with a dedicated API layer, organizations gain flexibility to evolve their automation architecture, while improving scalability, security, and operational control.
Identity & Access Management (IAM)
Without strong identity and access control, automation becomes a risk rather than an advantage. IAM is foundational to secure automation. A scalable IAM framework should include:
- Authentication (who you are)
- Authorization (what you can do)
- Auditability (what was done and by whom)
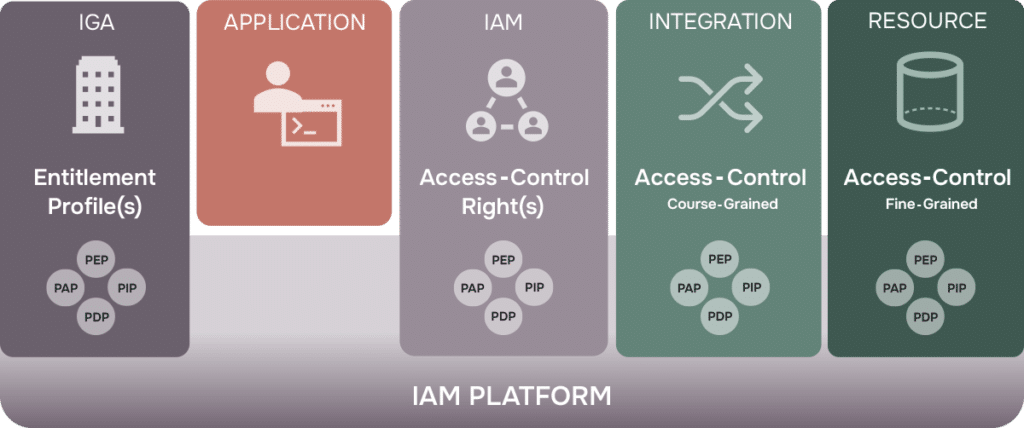
Treat IAM as a design pillar, not an afterthought. It’s key to enabling safe and accountable automation at scale—especially when automation spans multiple teams, domains, and security boundaries.
Learn how identity and access management fits into a broader strategy for securing critical digital services: Explore our secure IAM practices.
Assurance: Beyond Fulfilment
Service automation is not complete without assurance. Provisioning a service is only part of the lifecycle — validating that it’s working and performing as expected is equally critical.
Automation must include service verification and monitoring. Orchestrated assurance ensures:
- Proactive validation of services post-provisioning
- Faster detection and resolution of misconfigurations
- Basis for closed-loop automation and self-healing networks
Unified Operations Portal
To make automation accessible and operationally effective, organizations need user-friendly interfaces that bridge the gap between automation logic and daily operations.
An intuitive portal ties together orchestration, telemetry, and user actions:
- Launch or approve workflows
- Monitor service health and operational KPIs
- Integrate feedback loops into daily operations
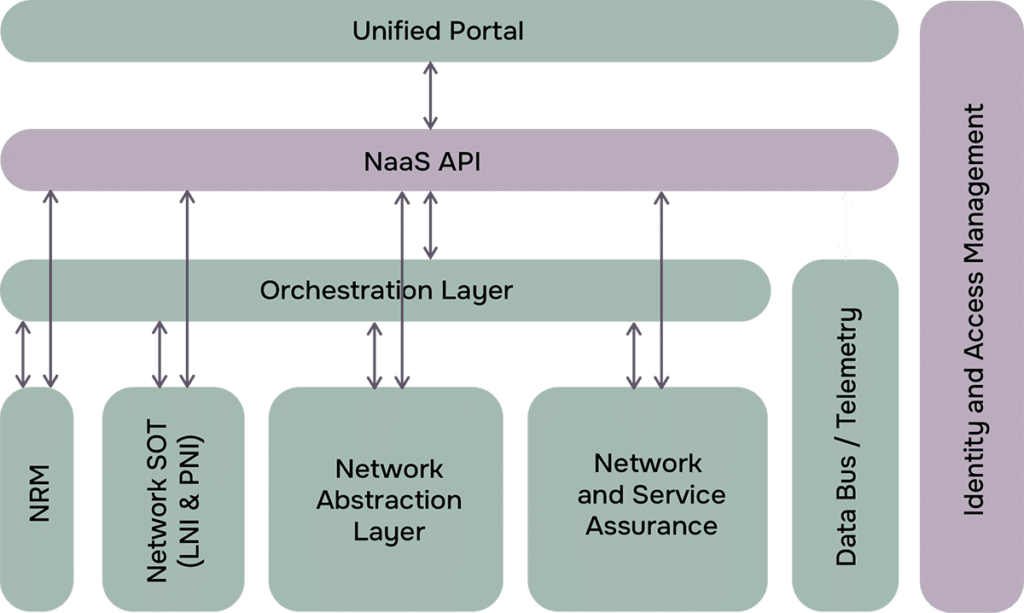
At Ductus, we’ve developed portals tailored to specific customer workflows — from provisioning triggers to change approvals.
Observability for the Automation Stack
Just as networks require observability for health and performance, so too must automation layers be instrumented. Treating automation workflows as first-class citizens in your observability strategy is key.
Automation itself must be observable:
- Collect traces, metrics, logs across the automation stack
- Use OpenTelemetry or similar frameworks for backend integration
- Ensure visibility into orchestration decisions and outcomes
Observability improves reliability and shortens recovery time. It ensures teams can quickly trace issues, verify outcomes, and continuously refine automation workflows for better resilience and efficiency.
Event Channel & Event-Driven Architecture
As network automation grows more dynamic and responsive, event-driven architecture plays a pivotal role in enabling real-time coordination and decision-making. An event channel acts as the nervous system of your automation stack, ensuring that changes in network state or service demand can be processed and acted upon immediately.
Key benefits of an event-driven model:
- Asynchronous processing: Decouples system components, allowing them to scale and operate independently
- Real-time responsiveness: Enables rapid reactions to faults, changes, or service triggers
- Workflow automation: Seamlessly triggers orchestration based on telemetry inputs or external systems
- Improved resilience: Enhances fault tolerance through distributed, loosely coupled components
To support this, the architecture should include a reliable event channel that connects automation layers without introducing tight dependencies.
Common tools: Kafka, CloudEvents, RabbitMQ
Ready to Future-Proof Your Network?
Success in network automation doesn’t depend on picking the perfect tools. It depends on designing an architecture that makes tools work together — and allows them to be swapped or scaled without breaking the whole system.
At Ductus, we’ve helped CSPs and global enterprises simplify operations, increase service velocity, and reduce long-term costs through modular, architecture-led automation.
Let’s talk. If you’re ready to build a network automation foundation that scales with your business, we’re here to help.

Peter Sallenhag
peter.sallenhag(at)ductus.se
Phone: +46 70 571 05 82









