
INSIGHT
One Secure Organization – Policy-Based Access Control (PBAC) for Enhanced Security
In part two of our series on one digital organization, we explore distributed authorization and access control and their roles in combining physical and digital security. If you haven’t read part one, where we covered the three-tiered approach to IAM, comprising an IAM Platform, IAM Framework, and IAM DevOps, as part of Zero Trust Identity Management, you can do that here. This time we take a deeper dive into Policy-Based Access Control (PBAC).
Strictly controlled premises
Once again, we consider the scenario of a large industrial plant, construction site, mine, server hall, or research lab, in which a broad range of external visitors come to the site regularly, whether it’s to deliver goods, service machinery and specialist equipment, or attend a meeting.
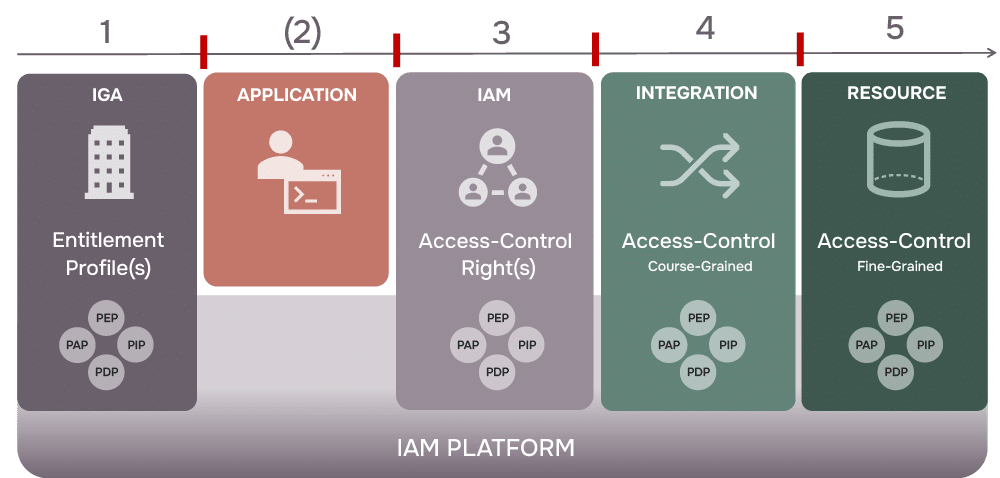
Policy-Based Access Control (PBAC) in short
PBAC is a dynamic authorization framework that regulates access to resources based on defined policies. It comprises four key components:
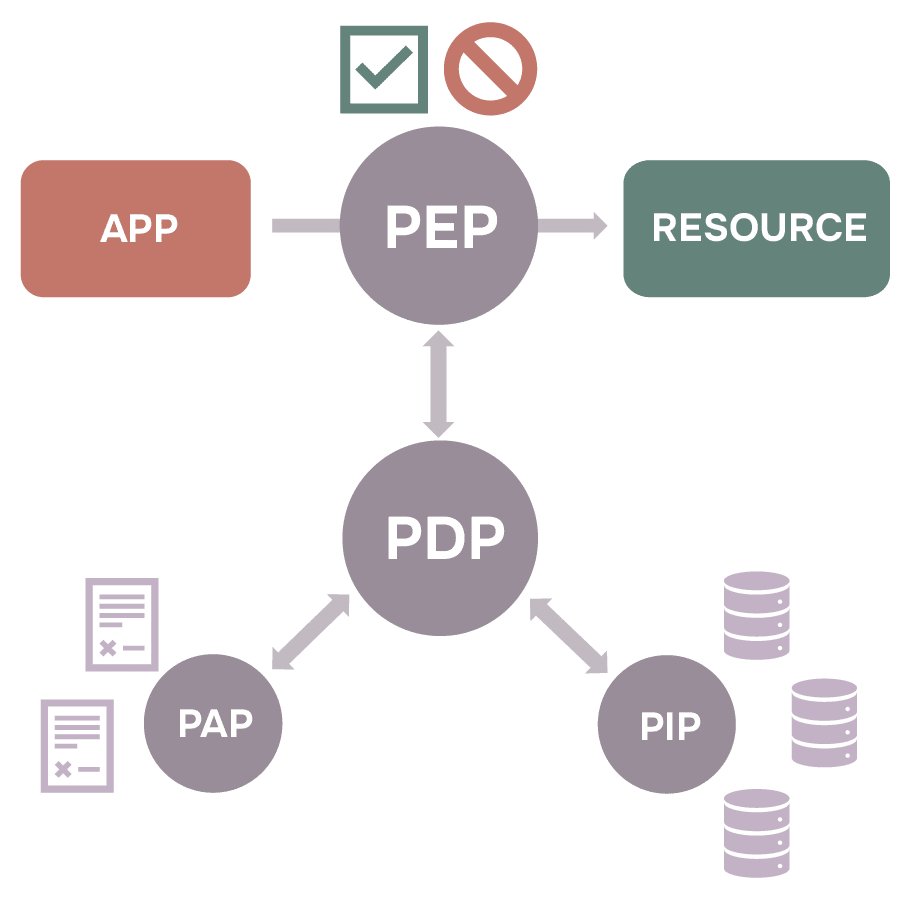
- Policy Enforcement Point (PEP): Serves as the gatekeeper, intercepting access requests from users or applications and forwarding them to the Policy Decision Point (PDP) for evaluation.
- Policy Decision Point (PDP): Evaluates access requests against established policies to determine whether access should be granted or denied.
- Policy Administration Point (PAP): Responsible for creating, storing, and maintaining the rules that govern access, ensuring policies are up-to-date and reflect organizational requirements.
- Policy Information Point (PIP): Acts as the source of contextual information needed for policy evaluation, supplying attributes such as user roles, company affiliation, and approved site access.
When an access request is made, the PEP forwards it to the PDP. The PDP consults the PAP to retrieve relevant policies and the PIP for necessary contextual information. Based on this data, the PDP renders an “allow” or “deny” decision, which the PEP then enforces, ensuring that access control is both dynamic and aligned with current policies.
Over-reliance on Identity, Governance, & Administration systems
Today, many companies with strict onsite visitor protocols rely on their existing Identity, Governance, & Administration (IGA) systems to manage visitor authorization. However, these systems are often heavily role-based, typically synchronized with directories like Microsoft Active Directory to reflect organizational structures.
While effective in some cases, this approach lacks flexibility and context awareness. For these companies, a broader, more dynamic solution would be beneficial—one that considers contextual factors beyond static roles. This is where Policy-Based Access Control (PBAC) comes into play, enabling more agile, vendor-agnostic access management that adapts to real-world scenarios.
Automating and Streamlining processes
Utilizing a distributed PBAC framework provides the ideal solution for automating and streamlining this process. This is achieved by grouping the activities into two key distinctions Authorization and Access Control.
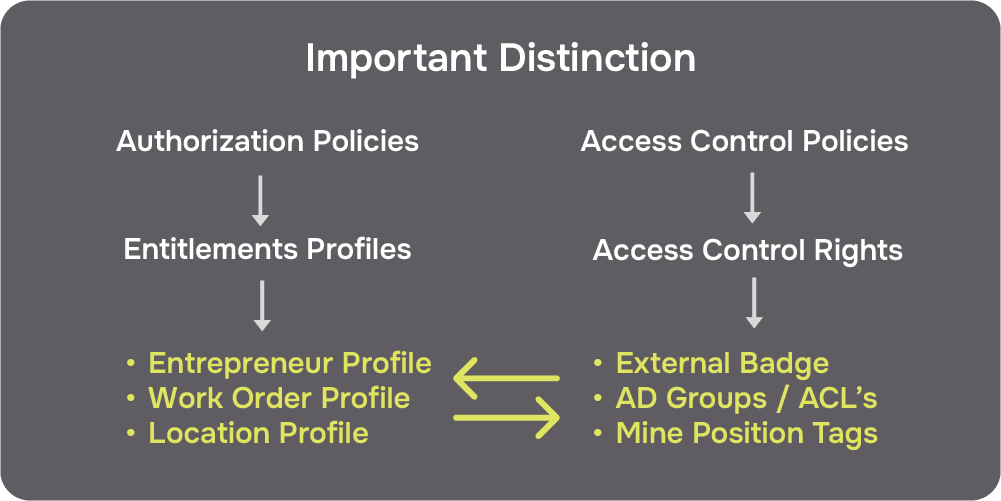
The Policy-Based Advantage
Authorization occurs in the initial visitor request phase whereby policies are used to check the entitlements of the contractor, company, work order profile, time slot, etc. These determine if, for instance, the contractor is approved to enter a particular section of a site at certain time to carry out a specific service. These policies are written by administrators in natural language as opposed to code, making it far easier for policy writers to own and manage the visitor security process. In its simplest form, a policy could be expressed as:
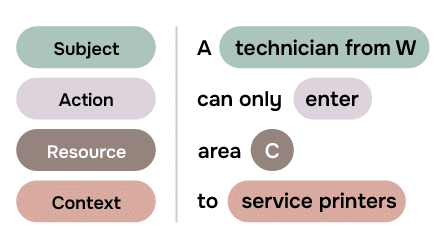
However, rather than simply being satisfied with the policy being approved or rejected, this system will also check to see if there are any over-riding policies for the particular visit. It could, for instance, be that during the summer months certain company’s technicians are approved to carry out additional printer servicing during July to cover for vacations. In which case, the overriding policy could be expressed as below. Similar policies could exist for an emergency situation or other scenarios.
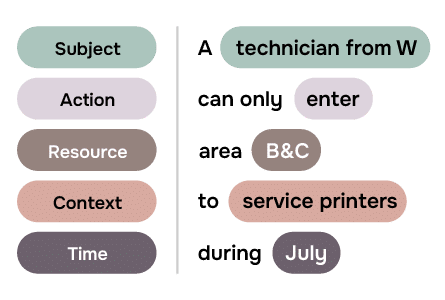
The Distributed PBAC Model
By implementing PBAC at the different touchpoints of the visitor request process, it’s possible to ensure a smooth flow from initial request through to badge printing, registration of vehicles parking permits, and gate and door access. The process can also be integrated with ERP, IGA and other relevant IT systems.
Get started
If you recognize these issues or want to develop a single security solution for physical and digital security but don’t know where to start, our consultants can support you. We recommend you begin with a particular pain point. Our team will define a PBAC framework along with a fit-for-purpose IAM platform, which can be run in a pilot project.
Don’t wait until it’s too late. Get in touch and let’s get started.

Anders Essner
Phone: +46 (70) 513 56 19
anders.essner(at)ductus.se
